Introduction
I really enjoyed writing my first story in November, and I received loads of great feedback so I thought I'd do another one but from a slightly different angle. As well as writing my usual posts writing these stories really helps me learn new and different things.So for my second effort I'm going to present a 3 part story. The first part will be the attackers story, the second and third parts will be the defenders perspective, focusing on the discovery of the attack and then some forensics thrown in for fun. I must point out that I am in no way trained in forensics, the techniques I will discuss would be those that any Systems Administrator could use to investigate an incident on his or her network after gaining permission.
Setting the Scene
As the title suggests this story will be about a rogue employee who feels poorly treated by his employers and wants revenge. His evil intention is to access restricted files and the sell plans for the eargerly awaited GNUphone to a popular website. Sounds easy? Well maybe I'll make things a bit interesting for him.
On the defending side is a keen Systems Administrator who looks after his network as if it's his baby. He has fought with management to have policies and procedures put in place to make his network secure.
So throughout December we'll see what the attacker does to get to the data, and what the Sys Admin does to try to prevent, detect and investigate the incident.
The Story of an Insider - Part 1. Shoulder Surfin Goodness
For a bit of background on this story you can read the intro here. This post details a low tech hack, primarily because its from the perspetive of a bog standard user. (If your reading this your probably not a bog standard user).
The Insiders story.
I've worked for this company for 2 years and all I get is crap from the boss. Those glory boys in design get all the praise for the GNUphone but if it weren't for people like me handling the suppliers and getting them down to rock bottom prices we couldn't even compete with the big boys in the market. It's launch day soon and all I see is the design lads getting party after party, rolling in late, taking long lunches and doing sod all. And to top it off I come in late once and I'm on a warning.
Well it just so happens that if I can just get the finished designs for the GNUphone to a guy I know over at MicroFone Magazine before the launch I'll be wiping the smile of those smug gits faces and I'll make a few quid too. I mean, it's not like i'm really hurting anyone, it justs means people get to see the phone a little early that's all.
I'll just have a poke around on the server and see what I can find...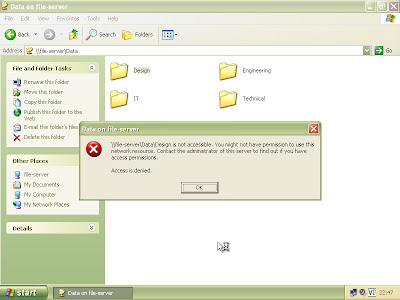
Bugger! I can't get in the folder. I guess only the superstars in design are allowed access. Well I know the top guy down there is a football nut so it wouldn't take the brains of an astronaut to figure out his password.
Well none of that worked. But Mark did get really pissed at Carl the IT guy because his account was locked out. Then the boss had a go too, ranting that the security was an overkill and was preventing people from working. Yeah right! More like preventing people from getting to Facebook.
Well I better think about this because I have got to get the designs, i've told my mate I can get them and I don't want to look stupid. I need some of those hacking tools but our Internet access and email is monitored and were not allowed to bring software in. Were not even allowed USB devices for crying out loud! The Sys Admin is so paranoid he's got bloody policy after policy preventing anything and everything. He needs to get a life!
Well I know the boss has had it in the neck from everyone about the password policies so maybe I can push things over the edge. I have the usernames for everyone, I'll just lock out the accounts by accessing the webmail with my Iphone using the other employees usernames and the wrong passwords, either the policies will go or the crazy paranoid Admin will. At the very least I'll have great fun watching everyone get pissed off. Am I a genius or what!
Well that didn't take too long, a day of selectively locking out all the bosses accounts and the account lockout policy has been lifted, now I can just guess away till my hearts content.
1 day later...
Well this guessing game isn't as easy as it would seem, I've tried the all the names of the players in his beloved football team and I'm still not in. Hang on, here comes Mark now, typically back late from his extended lunch break. I think I'll have a chat with him as he walks back to his desk.
I can't believe it, after a days worth of guessing passwords and he goes and types it in right in front of me as I'm chatting to him. All I had to do was ask him if he'd checked out the news about “his team” and he went straight to the Sky Sports website. What a Sucker! And after all that the password was the star strikers name and number. I should have guessed that!
Right, so now I have the login name and password of the guy who designed the GNUphone, all I have to do is find a way of getting the designs out of the office once I have them. I can't email them out, that's to risky. Thumb drives are still strictly banned, but I do have my other at home and it has a 2GB memory card. There's nothing in the policy that mentions phones! It's risky but as long as I'm discreet I should be able to hook up the cable and download the files to my phone. Brilliant!
Well the next day I get in nice and early and I have plenty of time to copy the files. I'll just hook up my phone behind the PC, log in as Mark and have a search round for the designs. All being well i'll have the designs on my memory card before long and I can get them over to my mate at MicroFone Mag tonight.
Crap, the boss is on walkabouts. I better get rid of this cable and phone before he comes over here.
Coming up..........The Sys Admins story.
The Story of an Insider - Part 1. The Sys Admin Storys
This is my second part to a fictitious story about a theft of Intellectual Property by an insider and the detection and investigation of the incident.
Strange, that's not a design computer he's logging on from. Oh here he comes now, I'll ask him.
Man, I can't believe that, I just got my ass chewed from his boss for the last 10 minutes because HE forgot his password. Well I've got stuff to do, maybe I'll take it up with him later when he's in a better mood.
The next day......
Well something is definitely going on. Either this is a wind up or someone is trying to hack my network. I've had nearly every manager kicking my ass today about the lock out policy, all within the last few hours, I've got a stack of reports to write and patches to test and now my boss wants me in his office. This is just great! I'll quickly raise the support ticket and get this on the system so I don't get an ass kicking for that too.
Well, I've been told in no uncertain terms that either the account restrictions go or I do. I tried to explain that this is more likely an attack of some sort because I have changed nothing on the network. No new software, no new policy settings, nothing. But it's no good, he wants the lockout policy gone immediately. It's a total knee-jerk reaction and he would not listen to reason.
Oh god, I hope it's not a virus or something, I better check the logs and see what's going on. We'll I found nothing in the AV logs, but there is definitely something wrong. In my Server event logs I can see loads of lockouts today.
I used EventCombMT.exe to get all the lockout events and export them to a file.

Eventcomb will rip through the eventlogs on the server and extract into text files just the event's I'm interested in. From the results I can see that accounts are being locked out, but from the IP of the OWA box.

It must be that its infected with a virus. There was only that PC in buying that got an account locked out too, I bet that's got the same virus.
Well from the logs on the OWA box I can see all the lockouts are coming from something trying to get in using valid accounts with a wrong password.

It seems it's always an iPhone that is locking out the accounts, I'll just grep through the other logs with PowerShell to see if this has happened before.
gc *.log | select-string "iphone"

It hasn't happened before but in the older logs I can see that an iPhone has only been used once before, and it was Pete in buying that used it. Interesting!
I still don't have too much to go on but doing something has to be better than doing nothing right! Maybe the PC in buying does have something to do with it.
Again the AV checks out okay and is up to date, the firewall has pretty tight egress filtering and those logs are pretty clean. If there was something bad on the network I would expect it to show up on the firewall or the proxy logs and there's nothing.
I checked the PC is up to date on security patches. Let me run a script on the PC and the OWA box to see what's running, there must be something wrong. I have a batch file I created to respond to incidents such as this.
REM Usage: filename.bat ip-address/hostname outputfile
@echo off set header1= **** Voliatile Data Gathering Script ****
cls
echo%header1% type get-vol.bat > %2
REM Start Date & Time
time /T >> %2
date /T >> %2
REM System
psexec \\%1 systeminfo >> %2
REM Processes
psexec \\%1 tasklist >> %2
psexec \\%1 tasklist /svc >> %2
REM Networking
psexec \\%1 ipconfig /all >> %2
psexec \\%1 arp -a >> %2
psexec \\%1 netstat -anob >> %2
psexec \\%1 nbtstat -s >> %2
REM Finish Date & Time
time /T >> %2 date /T >> %2
The script isn't perfect because it's using the executables on the PC which could have been compromised, but it'll do for now until I can get round there and run something locally.
remote-info.bat gt-buy-01 c:\results-gt-buy-01.txt
The script runs commands that gets me details of the running processes, network connections, logged on users and all that sort of stuff. It's pretty good and I can really do with knowing what's happening on the PC right now.
Well the script ran fine, no weird processes, but there were some network connections to the file server in Design. Looking at my results file I can see that the NBTSTAT -s command shows some pretty big data transfers from the File-Server to the buying PC.

That's pretty weird, buying doesn't access files on that server they have there own server. I also saw that Mark from design had logged onto that PC. That's strange too, why would the Design Manager log onto a PC in buying to access his files? I'll update the Support Ticket and give him a call.
Well Mark from Design knew nothing about logging into a PC in buying. He said he has never logged onto any PC but his own and he is sure he has never given out his password.
I went back to my logs and I saw that my little HoneyPot has been tripped as well.

It's just a folder I set up that has object access logging on it. All the guys in design leave it alone and no one has any reason to go to it. That is no one goes to it if they now what they are looking for. Obviously someone doesn't know what they are looking for. Now I'm getting somewhere!

Now I know there is definitely something going on, and it looks as though someone has been accessing files that they shouldn't be.
I quickly check the profiles on the buying PC and sure enough it backs up what all the other tools have told me, Marks login has definitely been used on the buying PC.

I've informed my manager of what I have found, he has emailed me giving me permission to examine the buying PC whilst he has a chat with Pete in his office.
My goal at this point is to find out if an incident has occurred and then discover how this incident happened.











