What I didn't cover in that post was WMIC (Windows Management Instrumentation Command). If that previous post was say the equivelent of DOS Kung Fu then WMIC to me is the Ninjitsu of DOS.
The pupose of this post is to describe and list WMIC commands that can be used to derive information from a target, and that information could be useful to either a Sys Admin, a Malware Hunter or just a plain old Evil Attacker. As I will demonstrate WMIC can be used to modify settings also.
Used alongside the commands I listed in my earlier post on Command-Line Kung Fu, the commands listed here allow almost any operation via that simple DOS prompt with no additionally installed tools.
How to use WMIC
WMIC can be used interactively, by simply entering wmic at the command prompt, or non-interactively, by entering wmic followed by a command. I prefere the non-intercative method as it allows me to output to files easier or pipe the commands through a find command to filter my results. I do use the interactive WMIC shell if I'm just browsing around a remote system though as to allows me to set global variables (such as /node) which can be usefull.
WMIC commands are structured in the following way.
wmic [global_switch]
so for a simple example i might use:
wmic share list /format:table
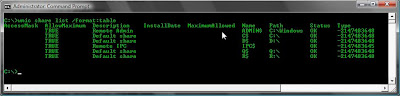
To use a global switch I might use the /node switch to query a remote host.
wmic /node:192.168.1.1 share list /format:table
To view a complete list of available WMIC commands and switches simply use wmic /?
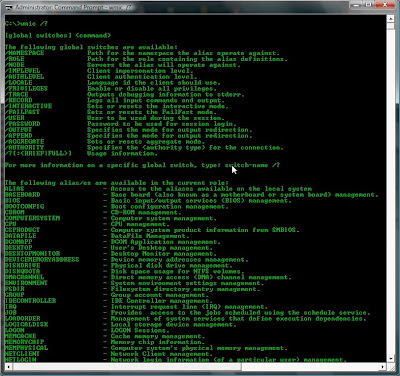
After finding the Global_Switch or Alias that i'm interested in I would use a command such as:
wmic volume /?
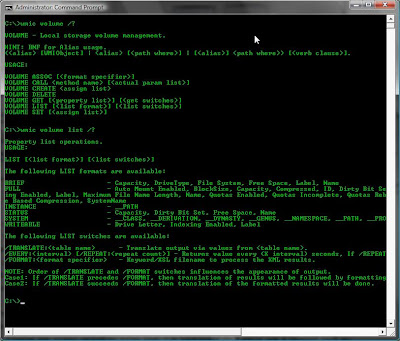
Or for the ultimate in output (but not in formating) try:
wmic /?:full
Output
The results of a WMIC query will by default go to STDOUT (the screen), however these can be output to a file using a couple of different options.
The /output option will output to a file:
wmic /output:c:\users.csv accountlist /format:csv
Or I can just use the greater than symbol to achieve the same:
wmic accountlist /format:csv > c:\users.csv
What I prefere about the second option using the > symbol is I can run the query to output to screen, if the output is as expected I can just simply bang a /format and >destination on the end of the command (i'm pretty lazy really!)
There are many options for the format of the output. I can view these by using the /? switch after the format command:
wmic share list /format /?
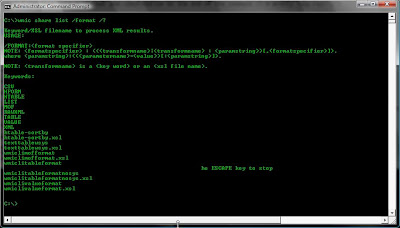
I can also choose to output only specific information if the normal output is to verbose by using the get clause. For example I might just want to list the IP Addresses on the network cards so I might use:
wmic nicconfig get description, ipaddress
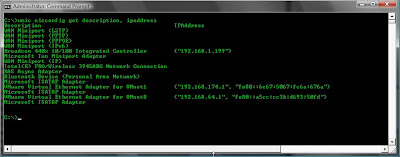
If the output is what i want i then simple use the up arrow on the keyboard to repopulate the line and put my format and output file on.
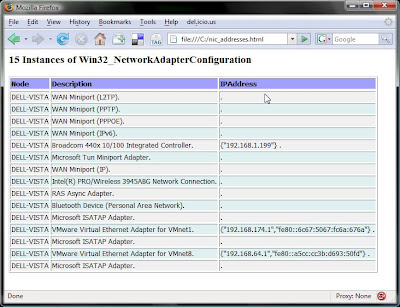
wmic nicconfig get description, ipaddress /format:htable >nic_addresses.html
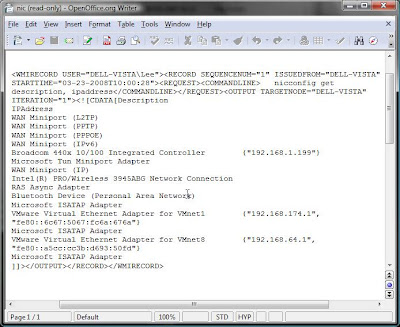
Finally one last ouput option I have come across on various websites is using the /record switch. This can only output to xml format but is very useful for recording the command typed, who ran the command, the output and the date. The resulting XML file can then be opened and viewed in Word.
wmic /record:nic.xml nicconfig get description, ipaddress
WMIC Commands
Okay, so now I have explianed a few of the basics of WMIC i'll get down to the fun stuff.
Remote Enumeration
Running WMIC without passing the /node: option will perform the query on the local machine. I could also run commands on remote machines in another domain (labnet in this example) by using the /user:"LABNET.CO.UK\Administrator" /password:"letme1n" options. An example of running a WMIC query on a remote machine in another Domain to get a user list may look like this:
wmic /user:"LABNET.CO.UK\Administrator" /password:"letme1n" /node:192.168.1.10 useraccaount list full
Or to use WMIC on multiple remote targets (assuming you have valid credentials) you could use the following:
wmic /node:@"c:\pclist.txt" volume get capacity, driveletter /format:htable >disk.html
With that out the way the examples that follow are all run locally. Some Examples I list the command to output to a file, others I will just list the output to screen.
Users
wmic /output:c:\users.html useraccount list full /format:hform
This gives me valuable information that the "net user" command doesn't, such as the SID which helps identify those renamed Administrator accounts.
Also dont forget the the sysaccount alias for those built-in accunts and groups
Groups
wmic group list full /format:hform >groups.html
This will list both local and global groups.
Shares
To list all the shares including hidden I would use:
wmic share list
Processes
To list the full details of the running processes and output the results to a file I might use:
wmic /output:c:\processes.html process list full /format:hform
Slightly easier format to read might be:
wmic /output:c:\processes.html process list full /format:htable
Or to filter out some of the utput I might pipe the results though a find command:
wmic process list brief | find "cmd.exe"
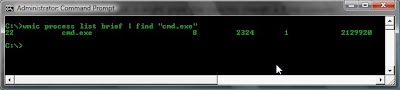
After listing the process information I might use the following command to Kill a processes by it's PID:
wmic process 2324 delete
or by it's name:
wmic process where name='cmd.exe' delete
Or if I want to display the processes and have the results update every 2 seconds I might use:
wmic process list brief /every:2
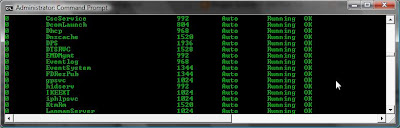
Services
To list the services that are configured to run at startup I might run the following.
wmic service list full /format:htable >service.html
Or to filter on just the running services that are set to startup automatically I might use:
wmic service list brief | find /i "running | find /i "auto"
Software
I might want to list the software that is installed. To do this I might use:
wmic os list full /format:hform >os.html
Service Packs and Hotfixes -qfe (Quick Fit Engineering) will list which service packs and hot fixes are installed.
wmic qfe
I can output this to a nicely formated file using the command below:
wmic /output:c:\qfe.html qfe list full /format:htable
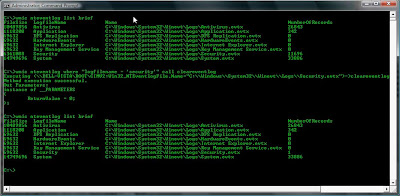
EventLogs
Event logs are important to both the Forensic Investigator and the Attacker. A forensic Investigator might want to use WMIC to copy the logs off the Victim PC by using thefollowing command:
wmic nteventlog where "Logfilename = 'System'" Call BackupEventLog "c:\systemlog.evt"
Okay, so how might an attacker use WMIC to make forensics more difficult? Well they might erase event logs.
wmic nteventlog where "logfilename = 'security'" call cleareventlog
And then to confirm that the log is erased the attacker might simply list the size ofthe log using:
wmic nteventlog list brief
Network Settings
When enumerating a target I can use WMIC to produce some output on the targets network settings. The Network card configuration is always useful to have. The command below gives me a nicely formated file with all the network card settings.
wmic /output:c:\nics.html nicconfig list /format:hform
This will list all the cards and the index numbers. From here I can identify a card and then maybe adjust the settings, dns for example.
wmic nicconfig where index=4 call enablestatic("192.168.1.10"), ("255.255.255.0")
wmic nicconfig where index=4 call setgateways("192.168.1.1")
wmic nicconfig where index=4 call setDNSserversearchorder ("192.168.1.100", "192.168.1.101")
Or to set the interface back to DHCP i would use:
wmic nicconfig where index=4 call enabledhcp
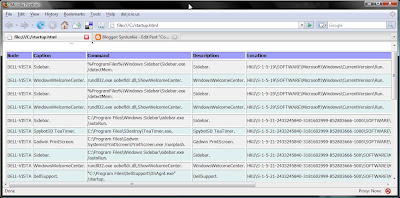
Startup
If hunting malware on a PC I might want to take a good look at what is going to be set to startup. The following command will list all those details and output it to a nicely formatted file.
wmic startup list full /format:htable >c:\startup.html
Starting and Stopping Applications
After listing running services and processes as shown earlier an attacker may use WMIC to stop AV software before running his evil program.
To stop an application, such as an anti-virus program:
wmic process where name="ashserv.exe" call terminate
To start an application:
wmic process call create "C:\evilprogram.exe"
And if I wanted to make sure the AV didn't start automatically I might use:
wmic service where caption="avast! Antivirus" call changestartmode "Disabled"
Update - 05-01-09
Enable Remote Desktops With WMI
Thanks to a comment left by Netcowboy I discovered that WMIC under Windows Server 2003 has many additional options than WMIC under XP. One really useful option for me was the RDToggle command.
To check if a remote server has remote desktops enabled use:
wmic /node:"servername" RDToggle where servername="servername" get AllowTSConnections
To enable remote desktops use:
Both of these commands assume you have the correct privileges on the remote server to run these commands. if not use the /user and /password switches.
If you wanted to enable remote desktops from XP use the following instead:
wmic /node:servername path Win32_TerminalServiceSetting where AllowTSConnections=0 call SetAllowTSConnections 1
http://technet.microsoft.com/en-us/library/bb742610.aspx
http://www.vedivi.com/blog/2008/05/how-to-enable-remote-desktop-programmatically/

