Whilst reading the WindowsIR blog recently I came across a mention of a tool which I had forgotten about, Network Miner. I thought I would take another look at it as I do remember that it looked interesting but i didn't have the time before.
I found that by using Cain, Wireshark and Network Miner together I could have more sniffing fun than I can shake a big bag full of sniffing things at. I could do this sort of thing in Linux by using Driftnet, TCPdump, TCPExtract and Dsniff but I wanted a Windows equivalent because i'm sick like that.
What I wanted to do was to pull images, files, passwords and other data either out of the air or off the wire with as little work as possible. Cain did a lot of this but for the files I needed Network Miner. Here's how it went.
Tools
- Cain & Abel
- Network Miner
- Wireshark
Steps
1. First I fire up Cain and after selecting my network device I start the sniffer and I Arp scan the subnet.
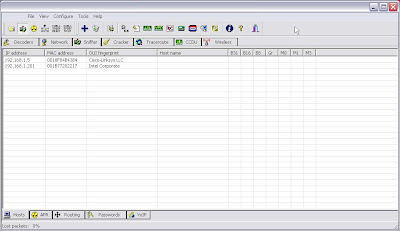
I can see that 2 hosts were found.
2. I then select the Arp tab at the bottom of the screen and select my hosts to poison.
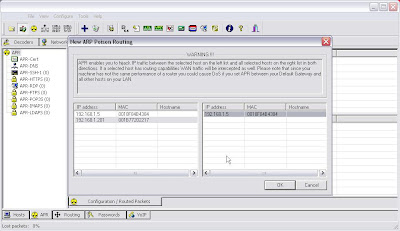
3. I then click on the Arp Poison button to begin the poisoning.
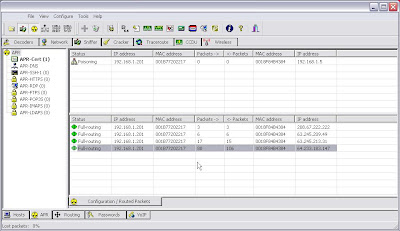
I can see Cain work it's charms and display the sessions in the bottom part of the screen. And if I check out the passwords tab I can see that my victim has logged into a couple of sites.
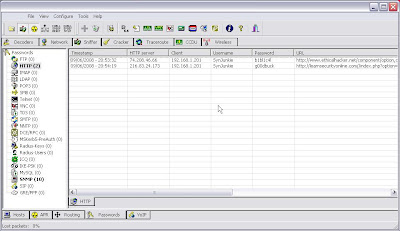
This is all good. But I want files and images too. Lets get Network Miner in on the action. Oh, and I want it wireless too because wireless is fun, right!
4. So I fire up Network Miner and it gives me loads of great information. Such as:
Juicy details on the hosts OS and the sites it has visited....
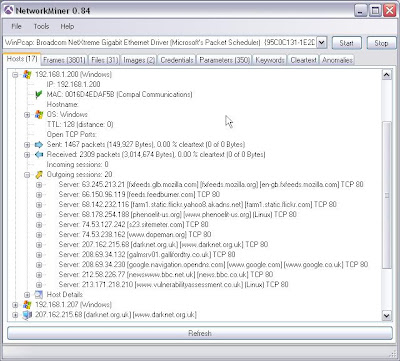
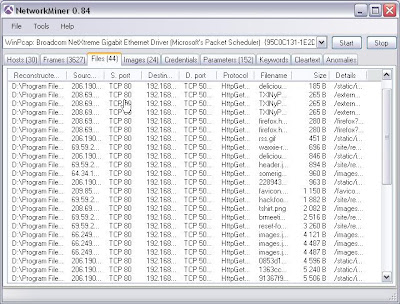
Files it has pulled down and where from....
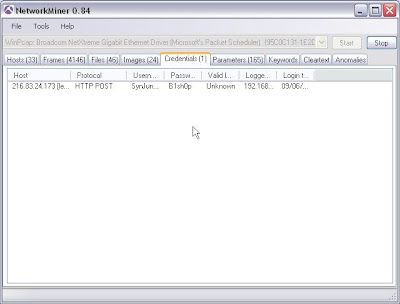
Yet more passwords........
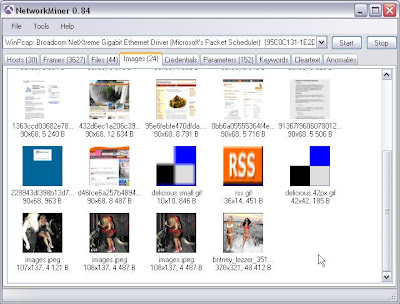
Fantastic images (driftnet for windows!)
Keyword searches on captured packets so I can see if my poor victim is search for something interesting......
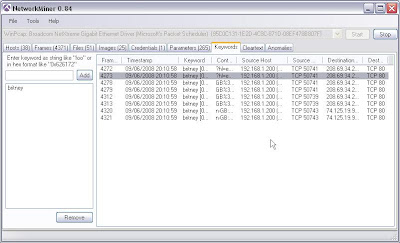
But this is all over the wire. And if I read the documentation for Network Miner it will tell me to do wireless I need an Airpcap WiFi card. Crap, that means I'm stuffed. Wrong, hello Wireshark.
5. I tear down my poisoning, enable my WiFi card, repoison a wireless victim in Cain using the same steps but with promiscuous mode turned of in the card options within Cain.
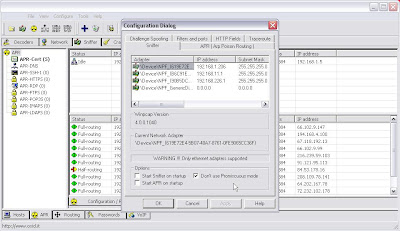
6. I fire up Wireshark and in the interface settings I also choose not to use promiscuous mode.
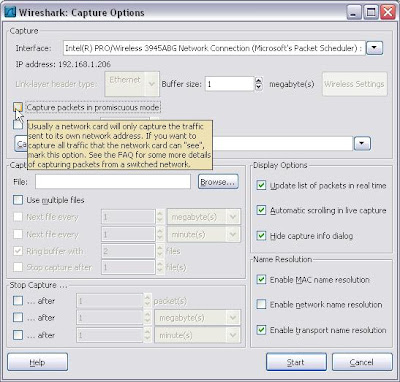
7. After capturing a fair amount of data over the wireless interface I save it to a .pcap file and then from the file menu in Network Miner I select open, browse to the .pcap file and Voila!
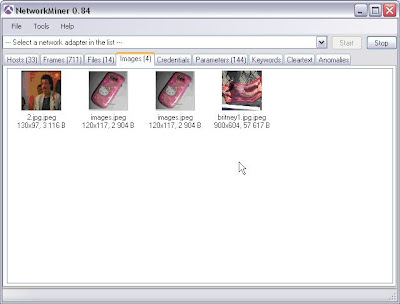
Thats it. I'm sure that much more fun can be had but thats all I had time for. Remember, get permission before doing any of this if it's not your network.

