Hping is a Linux tool that is run from the command line. What I really like about it is the control you have over the packet. If you dont have hping installed you can pull it down from most repositories.
Okay, firstly view the man page or use --help to list the many options to familierise yourself with hping.
Testing Open Ports
If i want to test for an open port I would issue the following command:
hping -i eth0 -c 1 -S 217.146.186.51 -p 80
Here i'm telling hping to use interface eth0 (-i eth0), send a single packet (-c 1), send a SYN packet (-S), to address 217.146.186.51, to send the packet to port 80 (-p 80), and to be verbose in the output (-V).
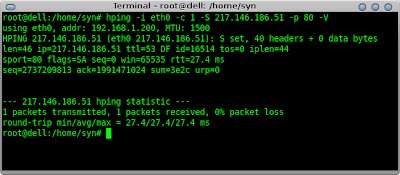
From the output in the screenshot you can see that the server returned a SYN-ACK so the port is open.
Below is a packet capture on that interface displaying exactly what was sent.
tcpdump -i eth0 -n -s 1514 host 217.146.186.51
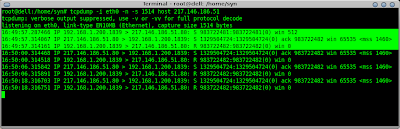
As can be seen the scanned host continues to send out a series of SYN-ACK packets after I have sent my Reset packet.
If I issue the command again but to port 81 instead you will see that the server doesn't return a packet. This tells me the port is probably blocked by a firewall.
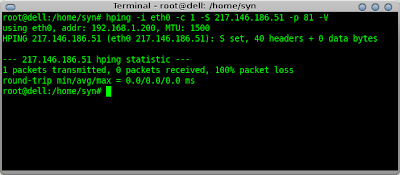
I can use a tool such as Nmap to confirm my hping results.
nmap -sS -p 80,81 217.146.186.51
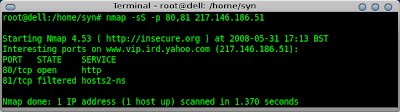
A packet capture of Nmap would have revelead that an ICMP echo request was initially sent when I issued the command above. This could have been prevented using the -P0 switch.
Back to hping, as expected if I issue the command to the host name instead of the IP hping attempts to resolve the address using DNS, this can be seen below in the tcpdump capture.
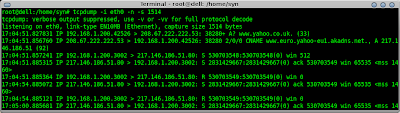
Another very useful switch is -s. When set it tells hping to use a specific source port. On one occasion whilst in a hotel I found that SSH traffic was blocked on port 22 but all TCP traffic was allowed on port 53. I then asked my wife to reconfigure my SSH server to listen on port TCP 53 and I was able to get back to my home network.
Port Scanning
Hping can also be used as a port scanner to test for a range of open ports. Using the --scan switch followed by a list of ports or a port range I can quickly scan a host.
hping -i eth0 --scan 20-25,80,443 -S 217.146.186.51
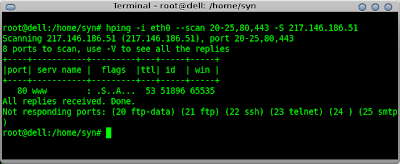
In the screenshot above I scan for a port range of 20-25 and also for 80 and 443.
Hping has many other function including more advanced firewall testing and file transfer. I'll cover these in another post.

