Sunday, February 7, 2010
The websites of two major providers of security products have been hit by hackers.
Leonard said: “The usual suspects have emerged as expected, with Valentine spam emails and Trojans. The public are becoming more aware of these and it is getting harder to trick people this way. Cybercriminals are also taking their efforts to social networks, given its rising popularity and potential to manipulate the user through ‘friend’ messages.
“Organised criminal units have a long history of timing their attacks to coincide with popular occasions in order to achieve maximum success. Valentine’s Day 2009 is a day that is similarly marked on the criminals’ calendar for targeted attacks.â€
Websense has warned of three key signs of fake sites: ‘Broken Hearts’ sites show colourful images such as puppy dogs or a picture of 12 pretty hearts and ask ‘Guess, which one is for you?’. The web page however is one big image and a single click from a tricked user commences the download of Trojans named “onlyyou.exe†or “youandme.exeâ€, which can connect to remote websites to receive commands and send information about the compromised system.
‘I am your friend’ uses social networking tricks to get users to visit fake sites, with Websense claiming that a popular technique at the moment is spam email pretending to originate from social networking sites – complete with love hearts and cartoon characters. Clicking through to the link would download a Trojan designed to steal log in credentials for banking sites.
Seventy per cent of the top 100 most popular websites either hosted malicious content or contained a masked redirect to lure unsuspecting victims from legitimate sites to malicious sites. Specially created malicious sites are in decline as cybercriminals switch to compromising ‘trusted’ websites. Websense claimed that as there is increased confidence in shopping and researching online - a lot of which happens whilst in the office – people are turning to the internet to order flowers, chocolates and other gifts and cybercriminals are compromising these sites and stealing data.
Leonard said: “The underground economy is positively flourishing as companies fail to keep up with security technology. Criminals are taking advantage of the growing number of Web 2.0 properties, which allows user generated content. More than ever we’re seeing websites injected with links to direct users to malicious and compromised sites.
“Since many email security systems lack web intelligence, spammers have also stepped up email campaigns which contain links to malicious web pages. It’s clear that businesses need security with real-time protection, but until this becomes the norm – cybercriminals will continue stealing data and breaking hearts.â€
source : http://www.hacking-news.com/
Wednesday, December 16, 2009
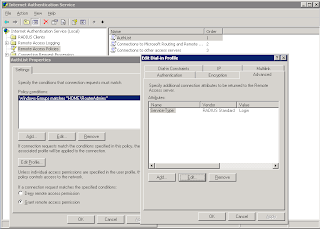
Using RADIUS to Authenticate Logins
- Create a Windows Security group with the users you want to allow access to the routers
- Enable the user accounts to have Dial-in Access.
- Install IAS on the server (from Add Remove programs).
- Create a new cisco RADIUS Client, point it to the Router and supply a shared key. Set the Grant Remote Access.
- Windows Group (point this to the group you created)
- Edit the profile and set the autentication to PAP
- Under the advanced tab set the service type value to login & remove Framed-Protocol.
After setting this up I also needed to configure RADIUS authentication on my Console port and Aux port using the following for each port:
Configuring Router Interfaces
Lab Setup
In this lab I'll have two router and I'll configure them to talk to each other
To start with you might want to clarify exactly which interfaces your router might have. This can be done visually (by looking at the device) or by using some of the excellent show commands.
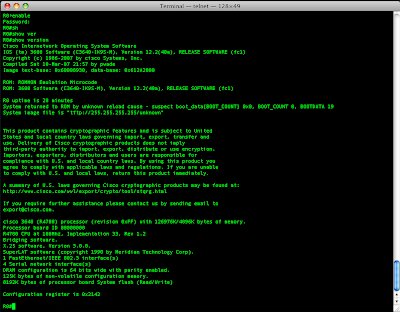
The show version command will print to the screen exactly which interfaces are installed.
R0>en
Ro#show version
The show interfaces command gives details on the configuration of the interface, setting such as duplex and speed, and it will also show traffic statistics.
R0#show interfaces
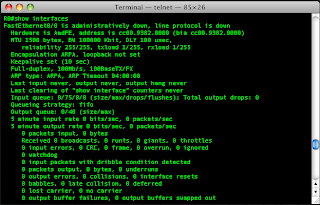
If you have many interfaces in your router you can just focus on a single interface using the interface number (remember, slot/port):
R0#show interfaces fastethernet 0/0
From the output I can see that the interface isn't configured. I'll configure that port and then take another look. I'll go into configuration mode select the interface, give it an IP address and subnet mask then tell it not to be in the shutdown state. Remember, by default all ports are in a shutdown state. Another import thing to remember is if you restore your config from a backup the ports will need to be taken out of the shutdown state manually.
R0>enable
R0#configure terminal
R0(config)#interface fastethernet 0/0
R0(config-if)#ip address 192.168.1.1 255.255.255.252
R0(config-if)#no shut
R0(config-if)#exit
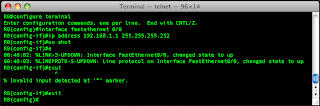
I saw the line come up when I was setting the port up, so now i'll ping my other router.
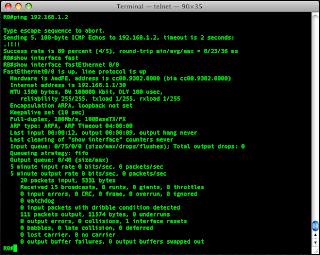
Wel the ping came back fine and after another look at the interface I can see it has the right IP address and the counters are updating nicely.
Another great command for looking at the interface is:
R0#show ip interface fastethernet 0/0
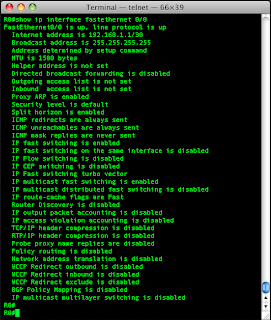
This shows me absolutely everything that is set or can be set on the interface.
And finally one last command for looking at the interface status in a nice condensed format is:
R0#show ip interface brief
Here I see all interfaces, what there IP addresses are and whether they are up or not.
So this has been a quick post on setting up an interface with an IP address and using some handy show commands to check the interface.
Securing Your Router
Right. So I've got my test lab set up. To start with i'll just have one router called R0. I'll demonstrate how to configure the router and secure it.
Securing Your Router
Right. So I've got my test lab set up. To start with i'll just have one router called R0. I'll demonstrate how to configure the router and secure it.
A Bit Of A Change - Yet Another Update
In the immortal words of Peter Doherty "Promises promises, I know, you've heard them all before...."
Getting Closer to God with Privilege Escalation
So rather than just focussing on holes in the Microsoft system, which frankly I'm not really talented enough to find much there, I decided to look at the configuration and implementation. In my opinion I would have much better luck looking for mistakes made by people not necessarily trying to secure a system but more trying to get a system to work.
In this post I'll focus a common mistake made by the guys who build the system which allows a standard user to escalate to have full system privileges.
Looking at Services
It would be nice to use WMIC to look for services that are in a directory that I can write to and that start automatically:
wmic service get name,startmode,pathname | find /i "auto"
However, when trying to run WMIC I get an error telling me that I need to be a member of the Administrators group. I could just go to the Services.msc but this means that I have to go through each service to get that path to the executable. A better tool I found for this is MSInfo32.exe

As can be seen in the screenshot I can quickly scan down the autostarted services for ones that have paths that I can write to. I also need the service to be running with an account with some decent privileges.
OK, VNC looks pretty good.
I go to the directory that VNC runs from and rename the executable. I copy Taskmgr.exe from System32 to the VNC directory and rename it as the VNC executable.

After a restart I see that I have no VNC in the system tray, so I go to the Services.msc and start it. Task Manager starts up for about a minute and then closes. Ok, that’s good. I start the service again and quickly launch a command shell before it closes, great now I have my system command shell. From here I can add accounts, change settings, install software etc... But maybe I want my full desktop. I launch Taskmgr.exe from the command shell, kill explorer from the process list and the launch explorer from File menu. Fantastic, I have a whole desktop running as System, now I really am closer to god!
Toying With Terminal Services
My aim was pretty simple, from a very locked down desktop I wanted to bypass the restrictions put in place and see how I could get to programs that the admin had tried to prevent me from getting to.
As we can see, all I have access to is a desktop with Notepad. No right click, Internet Options are restricted, the desktop is extremely locked down by group policies.

So once again I'm on the hunt for holes in the group policy so I can enumerate the domain and get to websites to post data or for additional tools etc...
As I start to hunt around I figured instead of accessing the desktop as I am supposed to, what if I configured my RDP client to launch one of the programs that I need straight after login instead of going to the desktop.

And what do you know........Bingo!

Although in group policy the admin could have restricted access to cmd.exe it's pretty hard to run login scripts etc.. so most admins won't, they'll just make it difficult to get to.
Of course this worked for launching an MMC also, and pretty much any program. Again the snappins for MMC's can be restricted in group policy but how many admins are going to go to that level?

Coming up.......More Terminal Services goodness.
Friday, October 23, 2009
DDoS, antara iseng dan kriminal, antara iseng dan kriminal
Ah Sapi lo !! maen DDoS² aja lo, biar gw kurang ngarti ma gitu²an trus kaga ada di tempat waktu itu, tapi tetep aja kaga enak ma yg punya warnet dul, klo mpe putus koneksi ntar gw juga yg kena, gila lo ye warnet temen sendiri maen lo DDos² aje
Masih inget banget tampang bete dari temen gw bung benz tapi tetap dengan cengengesan waktu dia ngomong gitu ke gw, ya gimana ga bete klo warnet tempat dia kerja gw isengin, yup iseng, gada motif laen selain iseng
Sebener’a sey berawal dari temen gw tukulesto yg lagi chat ma gw via yahoo messenger, iya bener tukulesto, panggilan’a tukul tapi dia fans berat tiesto, maka’a panggilan’a jadi tukulesto, tapi itu bukan nama aseli loch, nah cerita’a ketika gw lagi chating ma tukul via YM, dan saat itu lagi marak²a situs rapidshare and youtube di blokir ma pemerintah, eh tau² tukulesto ini private messege ke gw sambil ngebuzz, kira² percakapan’a kya gini:
T: yeeeAh !! rapidshare ma youtube jebol juga !!
G: hah !! gila lo ngejebol rapidshare ma youtube?!! (sambil memandang takjub)
G: Lo deface kul? apa lo bikin down server’a? sadis juga lo ye
T: bukan², mksud gw, gw bisa akses youtube ma rapid ney pk proxy
G: o0o… kirain kul, mana bagi dunk proxy’a, punya gw dah mati semua ney
G: cape gw bikin proxy molo, paling cuma awet 2 harian doank
G: mana? minta dunk? paste’in disini aja kul…
T: iye sabar², ini baru mo gw paste
G: sep
Akhir’a dia ngasih cukup banyak proxy server ke ym gw, entah kenapa dari sekian bnyk proxy yg dia paste, satupun gada yg gw pake, cuma ngeliatin aja sambil males²an nanggepin tuch anak dan entah kenapa juga niat iseng gw tau² muncul waktu gw ngeliatin beberapa nomor² IP address yg dia paste. Hmmm.. secara siang itu gw juga lagi dapet shell inject baru, sambil mikir dan trus bertanya dalem hati sendiri, kira² tukul kena ga yach klo gw social enginering ma dia, tapi masa sey segampang itu dia bisa di kibulin, ahkz coba aja dolo lah
G: eh kul² coba lo check ip public lo dey kul
T: mang knapa yan?
G: takut’a lo kena banned ma rapid gara² lo make proxy server
T: ah yakin lo?
G: lah masa gw boong sey ma lo(padahal dalam hati sey “emang gw boong”)
G: rapid tuch nolak klo lo pk proxy server, nah klo ketauan terus²an
G: ip lo bisa kena banned, maka’a mo gw check dolo, sapa tau bisa gw akalin
T: o0o… gimana cara’a yan nge-check ip address public gw
G: zZz²
T: ![]()
G: buka google trus ketik ip check, pilih aja situs yg pertama
G: nah di sono pasti kliatan ip public lo
T: ooohh
T: udah ney, udah tau gw nomer ip nich kompi
G: mana coba liat, sapa tau bisa gw akalin biar lo ga kena banned ma rapidshare
Dan seketika itupun dia langsung ngasih ip address public number’a secara cuma² ke gw, dan jelas dengan sangat sah gw ngakak abis, bener² bisa gw boongin ney orang
G: Bruakakakakak
T: napa lo
G: bego bener dah lo, bruakakakak
G: gw DDoS ye, iseng kul gada gawean ney gw, bruakakakakak
T: jangan dunk kaka, saya kan masih cupu kaka =(
G: hasyaahh, saya juga cupu kaka =)
tanpa basa basi busuk dan tanpa rasa belas kasian gw ke dia yg minta “jangan” ke gw, langsung aja gw load 5 server berbeda dari hasil pembuatan backdoor webshell dari shell inject gw yg baru, masing² server gw upload beberapa tool diantara’a Vadim.tgz dan UDP.pl yg langsung gw eksekusi dan langsung gw tembak ke ip address target
Yup 5 server sekaligus, begitu gw ping ke ip dia, ternyata traffic’a langsung naek dari 2 digit ke 4 digit or klo ga salah dari traffic time left’a sekitar 56 jadi 4850an lah, jelas gw ngakak abis di atas penderitaan temen gw, sekitar ½ jam tuch warnet gw DDoS ga pake rasa kesian dan ga brenti², tau² besok’a pas ketemu gw dia ngomong gini:
T: ah kampret lo, masa gw lagi download 6 file dari 20KBps turun drastis jadi 3KBps
G: hehehehe sori kul (sambil cengegesan masang tampang ga bersalah)
G: trus gimana kul? putus ga koneksi lo?
T: 1 koneksi kya’a putus, gw liat di billing server request time out panjang dul
T: akhir’a gw switch aja ke line koneksi yg kedua
G: sori kul sori, abis’a gada gaweans euy
dan lusa’a gw di caci maki lagi sama bung benz, nah dari kejadian nyata dan motif iseng diatas, apa itu termasuk ke dalam kriminalitas? yaiyalah masa yaiyadonkz, lalu bagaimana dengan salah satu berita yg gw kutip dari salah satu situs, seperti berikut:
Pemerasan Ala Hacker Makin Ganas
Pemerasan yang memanfaatkan serangan DDoS makin mengganas. Jika sebelumnya target adalah situs judi atau situs porno, kini situs keuangan masuk dalam daftar korban.
DDoS (distributed denial of service) adalah salah satu jenis serangan cyber favorit untuk melumpuhkan sebuah situs. Seperti banyak serangan di Internet, DDoS cukup akrab dengan dunia hacker.
Serangan itu, beberapa bulan terakhir, kerap digunakan untuk tindak kejahatan pemerasan. Pelaku serangan akan mengancam korbannya dengan serangan DDoS. Lazimnya pemerasan, korban dipaksa membayar sejumlah uang tertentu untuk menghindari serangan.
Target serangan biasanya adalah situs ‘remang-remang’ yang mengoperasikan perjudian atau konten porno. Namun parahnya, modus itu mulai merambah ke situs pemroses transaksi kartu kredit.
Hal tersebut terjadi pada situs Authorize.net. Situs tersebut merupakan penyedia jasa proses transaksi kartu kredit. Authorize digunakan untuk menentukan validitas data kartu kredit pelanggan dan bisa juga untuk mencegah pencurian kartu kredit.
Sekali Dayung, Dua Tiga Pulau Terlampaui
Sampai dengan tanggal 22 September waktu setempat (Authorize.net berbasis di Amerika Serikat -red.) Authorize.net masih mengalami serangan secara acak. Sebelum serangan dimulai, Authorize mengaku menerima surat pemerasan.
Naftali Bennet, CEO perusahaan keamanan internet Cyota, melihat ‘manfaat’ ganda yang didapatkan dari serangan terhadap Authorize dan penyedia jasa sejenis. “Sementara layanan online mereka mati, transaksi bisa jadi harus diproses secara manual lewat telepon. Ini akan menyebabkan penundaan, dan dapat menguntungkan pengguna kartu kredit palsu (carder -red.),” tuturnya.
Serangan DDoS, ujar Bennet, sebenarnya berawal dari pekerjaan iseng. Namun hal itu berlanjut jadi kegiatan kriminal saat dibarengi dengan pemerasan. “Biasanya calon korban adalah situs judi atau situs porno, pasalnya status mereka yang ‘remang-remang’ akan membuat mereka malas menghubungi polisi dan lebih memilih untuk membayar,” Bennet menjelaskan.
source : venom's Blog