Another interesting attack, rather than going after the PC/Server this one goes after the data sent by wireless devices such as the wireless keyboards sold by Microsoft. The neat thing is by using a replay attack you could also send rogue inputs to the device.
But then it serves Microsoft right for using XOR encryption for the data-steams, which can very easily be broken using frequency analysis.
Security researchers on Friday unveiled an open-source device that captures the traffic of a wide variety of wireless devices, including keyboards, medical devices, and remote controls.
Keykeriki version 2 captures the entire data stream sent between wireless devices using a popular series of chips made by Norway-based Nordic Semiconductor. That includes the device addresses and the raw payload being sent between them. The open-source package was developed by researchers of Switzerland-based Dreamlab Technologies and includes complete software, firmware, and schematics for building the $100 sniffer.
Keykeriki not only allows researchers or attackers to capture the entire layer 2 frames, it also allows them to send their own unauthorized payloads. That means devices that don’t encrypt communications – or don’t encrypt them properly – can be forced to cough up sensitive communications or be forced to execute rogue commands.
It’ll be interesting to see what other kinds of devices they can successfully use this data capture technique on. Keyboards are one thing, and I’d imagine the transmission range of a wireless keyboard is fairly limited so you or the sniffing device would have to be physically near to the target.
At least Logitech seem to have stepped up the security a bit by using AES-128 for the transmission on their wireless keyboards, but the researchers say they still may be able to crack it due to the way the secret keys are exchanged.
Again most likely not an algorithm problem but an issue with the implementation.
At the CanSecWest conference in Vancouver, Dreamlab Senior Security Expert Thorsten Schroder demonstrated how Keykeriki could be used to attack wireless keyboards sold by Microsoft. The exploit worked because communications in the devices are protected by a weak form of encryption known as xor, which is trivial to break. As a result, he was able to intercept keyboard strokes as they were typed and to remotely send input that executed commands on the attached computer.
“Microsoft made it easy for us because they used their own proprietary crypto,” Schroder said. “Xor is not a very proper way to secure data.”
Even when devices employ strong cryptography, Schroder said Keykeriki may still be able to remotely send unauthorized commands using a technique known as a replay attack, in which commands sent previously are recorded and then sent again.
News time is always fun during conference season due to the fact all these interesting and new attacks and vectors are released for public consumption – generally along with code and examples.
If they can use the same techniques to own more interesting devices with more sensitive data, things could certainly get a little more heated.
source : darknet.org.uk
Showing posts with label wardriving. Show all posts
Showing posts with label wardriving. Show all posts
Friday, April 2, 2010
Tuesday, December 15, 2009
Bob and his iPhone Adventures
So in the last post I blogged about a cool tool that our super hero, evil Bob, might use to find wireless networks when out with his super fantastic iPhone. Well after tracking down those pesky open networks I image the next thing Bob might want to do is look a bit deeper into a particular network. Well a great iPhone application for doing so is called Snap, and it works like this.
Bob is out and about with his trusty iPhone and he stumbles across an open wifi network. Bob being Bob, he connects to the network and gets himself an IP address, so far so good. But his curiosity gets the better of him and he wonders what else is on the network with him. So he fires up Snap and kicks of a scan.

Snap scans picks up the subnet that Bob is on and automatically scans for live hosts. After a second or two Bob sees a list of who else is on the network with him.
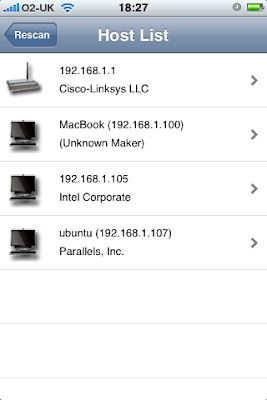
Interesting. Well Bob could leave it at that. After all, his curiosity is nearly satisfied, but not quite. He feels the urge to see what the other hosts on the network are doing, just to be sure that they are alright and not up to no good. So he drills down a bit further and takes a look at the Ubuntu VM.

Well Bob wouldn't be called nosey Bob if he didn't then go ahead and do a little port scan would he.

What do you know. VNC and a web server. That's just great. now Bob is satisfied. He knows who's on the network and now he has had a little poke around and he know what they are doing.
But hang on. Bob just remembered that old saying, "hard on the outside and soft on the inside" . Well maybe just before he goes he should put that to the test. He fires up his iPhone VNC client and tries a few common passwords.

And after a couple of attempts he gets lucky with......you guessed it "Password".

Bob is out and about with his trusty iPhone and he stumbles across an open wifi network. Bob being Bob, he connects to the network and gets himself an IP address, so far so good. But his curiosity gets the better of him and he wonders what else is on the network with him. So he fires up Snap and kicks of a scan.

Snap scans picks up the subnet that Bob is on and automatically scans for live hosts. After a second or two Bob sees a list of who else is on the network with him.

Interesting. Well Bob could leave it at that. After all, his curiosity is nearly satisfied, but not quite. He feels the urge to see what the other hosts on the network are doing, just to be sure that they are alright and not up to no good. So he drills down a bit further and takes a look at the Ubuntu VM.

Well Bob wouldn't be called nosey Bob if he didn't then go ahead and do a little port scan would he.

What do you know. VNC and a web server. That's just great. now Bob is satisfied. He knows who's on the network and now he has had a little poke around and he know what they are doing.
But hang on. Bob just remembered that old saying, "hard on the outside and soft on the inside" . Well maybe just before he goes he should put that to the test. He fires up his iPhone VNC client and tries a few common passwords.

And after a couple of attempts he gets lucky with......you guessed it "Password".

More Iphone Wardriving Goodness
WiFiFoFum have upgraded their Iphone application and I thought it was well worth posting about because it's making great use of the inbuilt GPS on the 3G Iphone.
We still have the Radar and Networks view.

But now you have the option to enable logging before a wardrive. In the screenshot below you can see a few previous logs.

After creating a log from a wardrive you will be able select it and you'll be asked if you want to view it in Maps or email it to yourself.

If I choose to view the log in Maps I get taken straight into maps and I'm presented with a nice map of all the AP's I discovered on my wardrive.

If you choose the option to email yourself the .kml file you can simply save the file to your PC and then drag and drop the .kml file into Google Earth to see exactly where everything is.

How cool is this eh! The pins retain all the useful info such as encryption, channel number, MAC address etc.....

What would be great would be a different colour pin to denote different types of encryption, but I guess that's making life real easy.
Now go get yourself some exercise and get wardriving!
We still have the Radar and Networks view.

But now you have the option to enable logging before a wardrive. In the screenshot below you can see a few previous logs.

After creating a log from a wardrive you will be able select it and you'll be asked if you want to view it in Maps or email it to yourself.

If I choose to view the log in Maps I get taken straight into maps and I'm presented with a nice map of all the AP's I discovered on my wardrive.

If you choose the option to email yourself the .kml file you can simply save the file to your PC and then drag and drop the .kml file into Google Earth to see exactly where everything is.

How cool is this eh! The pins retain all the useful info such as encryption, channel number, MAC address etc.....

What would be great would be a different colour pin to denote different types of encryption, but I guess that's making life real easy.
Now go get yourself some exercise and get wardriving!
Subscribe to:
Posts (Atom)

