Basically, what i'm going to demonstrate in this post is how the SMTP service on an Exchange Server can be abused. It's quite trivial to send a message to someone else using an Exchange server without having a mail account. And as I'll demonstrate also, it's quite easy to spoof your IP address so even if they examine the headers they'll never know where it came from.
Now, why is this useful to an attacker? Well firstly I can send a message to someone and link to a file. If the reciever usually trusts that person I'm pretending to be they will likely click on the link. Secondly, I can spam the world and become a small time spam king and attract many beautiful women.
Bear in mind that the SMTP stuff can be done with telnet to any SMTP server but the IP Spoofing will only work if you are on the same subnet as it uses Arp poisoning.
Okay, heres how it goes.
Tools
>Sterm or Telnet
Method
1. Find a Exchange mail server by either sniffing traffic or scanning for servers with port 25 open
2. Launch Sterm. Select configuration, and enter the IP you want to spoof and the MAC address you want to spoof.
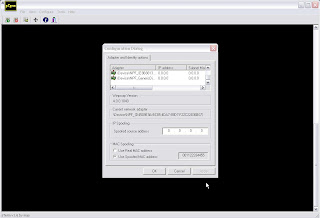
When I played a joke on a certain individual I did my homework and made sure these tied into the same addresses as the person I was spoofing.
After specifying the spoofing settings click on the file drop-down menu and select connect. you need to then enter the IP and port which you want to connect to.
3. At the prompt type :
helo servername.domainname.com
Obviously the FQDN should be used. You could also just type "helo IP-Address" with IP-Address being the one that you are spoofing.
4. Now we would enter who the message is going supposedly from:
mail from: blobby.knob@company.com
5. Now we enter who the message is to:
rcpt to: poor.victim@company.com
Often this address needs to be an internal address as mail relay may be turned off This can be testd though by sending a message to throw-away webmail account.
6. Now we specify the data we are going to send.
data
After typing "data" you should recieve the response 354. This means that you can send data.
7. Enter a subject line and press return:
subject: check this out!
8. Enter some aluring text:
Does my arse look big?
http://goatse.unfg.org/asciigoatse.htm
9. Now finsh the message buy pressing return, entering a period, and pressing return again.
The server should send a 250 code indicating the message is queued. Type quit to finish.
Now, when the recipient get the message they think its from the person it said in the senders details and they will follow the link and ........... well thats what you get for following links right!
Should they look at the headers they will see the spoofed IP address.
As I said, this can be done with Telnet but the IP spoofing part needs Sterm.
Oh and one last thing. Sorry Paul, it was just a joke.

