This blog entry is primarily for me to give as a reference to friends and family who ask me about the best way to secure the wireless connection. I will attempt to not focus on any vendor specific wireless routers i.e. Linksys, Netgear, etc… and focus on the basics of wireless security instead. Throughout this blog entry i will use the terms Wireless Access Point (WAP), Wireless Router and router interchangeably.
Many wireless routers do not have security features turned on by default. The reason for this is so when you get the router home you can plug it in and it will work quite seamlessly. At this stage your router is in what is known as an Open Wireless Configuration. This may seem all well and good but there are some serious downsides. I detail these below.
- If you can connect to the router quite easily and seamlessly then anyone who is within range of the wireless signal can also.
- Anything someone does who is using your internet connection will point back to you. This could be downloading illegal files, downloading pornography, illegal fileshareing etc…
- If another computer on your Open Wireless Network has a virus it can easily infect your computer.
- Anything you do on the internet, such as banking or email, may be seen from other computers connected to your wireless connection.
- Your internet connection may become slower due to sharing your bandwidth with other people connected to your wireless network.
Hopefully the points listed above illustrate why it is important that you secure your wireless connection.
To secure your wireless connection I recommend a layered approach. This means that you have multiple layers of defence. If one layer fails then another layer is in place to still provide some security.
The layers I suggest are as follows:
- Change the routers default password.
- Change and hide the routers default SSID.
- Implement MAC Address filtering.
- Configure Encryption.
- Harden the routers configuration.
Change the Routers Default Password
You will often be brought to a login page requiring a username and password, again these will be supplied. Now here’s the thing. These supplied credentials the same for the router for everyone who has brought that model router so quite a few people will know them. There are also websites that list usernames and passwords for popular models. They are easy to find on the internet and I have listed one below.
http://www.phenoelit-us.org/dpl/dpl.html
So as you can see it's important to change the password from the default.
Look for a page or tab that comes up called something like General, or Administration or Advanced. Each Router is different so you may need to click around a bit until you find it. Change the password to something that is difficult to guess, something that is quite long and something not in a dictionary. Write this down and keep it private and safe where you will be able to find it when you need it.
Change and Hide the Default SSID
The SSID is the name that your router broadcasts out to identify itself. Again, when you get your router this is set to a default, such as Netgear or Linksys. Now the problem with this is the following:
- The default SSID will tell other people what equipment you have. If a problem is found with your model of router that is publicly disclosed it makes an attackers job easier to find a vulnerable router. i.e YOURS!
- If you have a SSID of Linksys and one of your neighbours has a default SSID of Linksys, you may be connecting to the wrong Wireless Access Point (WAP). Information you send over the internet could easily be seen by your neighbour.
As well as changing the SSID to something unique but not obvious, such as your house number or your name, you prevent somebody acedently connecting to your WAP by mistake. You also prevent people from guessing the type of WAP you have.
Hiding the SSID is another layer of protection. Admittedly, it won’t stop a determined attacker from discovering it but it will stop the average computer user from seeing it. Sometimes it may be easier to hide the SSID once you have connected to it with encryption and things are working. So it may be an idea to come back to this one at the end.
MAC Address Filtering
MAC Address filtering, sometimes known as Hardware Address Filtering is another measure you can take to protect yourself from someone using your WAP to access the internet. All network cards in computer, both wireless and normal network cards, have physical (MAC) addresses. One way to view the MAC address is to bring up a DOS prompt (Start Menu > Run type “cmd” press OK), at the prompt type:
Ipconfig /all
You will then be presented with a screen of information similar to that on the screenshot below.
As you can see, the physical address of my wireless network card is:
By using MAC address filtering I would enter this number into the configuration on the WAP to instruct my WAP only to let network cards with that address to connect it. Below is an example screen from my wireless router admin page where I set up MAC Address Filtering.
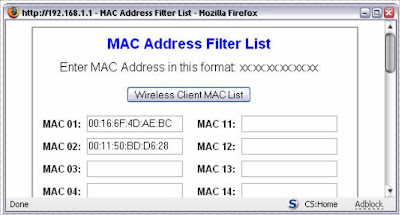
Depending on your model of router you may have to search around for this page. A good bet is in Wireless Settings, or Wireless Security.
If you have people visit you and they want to use your access point you will have to update your router with their MAC address. If you want to administer the router from another computer should yours become unavailable you will have to use the wired connection and physically connect to the router to make changes.
MAC Address Filtering is not a strong security measure and a determined attacker will be able to bypass this. An attacker could do this is because at this stage your traffic is still unencrypted. He could simply look at the traffic with what’s called a sniffer and easily determine the MAC address that you are using. He would then change his MAC address to be the same and he could once again use your internet connection.
All you have done so far is secure the WAP and raise the bar slightly and prevent your access point from being used by someone else.
Encryption
The next step is to encrypt your traffic. The reason for doing this is privacy. It is important to remember that by applying encryption, your traffic is only encrypted between your computer and the WAP i.e your wireless router. Once the traffic gets out onto the internet it is often (but not always) back in clear, but this is fine because there is so much traffic that yours is just mixed up with all the other internet traffic.
If you are using a site where the URL (the address of the website) begins with https then your traffic is encrypted between your computer and that site. Your banking site, sites where you shop or enter a password or enter credit card details should always have addresses which begin with https and are thus encrypted.
There are different types of encryption available on most home wireless routers, WEP and WPA2. I will cover the basics setting up both encryption protocols even though WEP is not very secure and should only be used if WPA2 (or WPA) is not available.
The following is method I use for setting up WPA2 or WEP in Windows XP.
- From the Start Menu > Control Panel > Network Connections. View the properties of the wireless network card. From the Preferred Network list check the properties of the Wireless Access Point and identify which encryption protocols and algorithms your computer supports.
- Connect to the wireless access point (WAP) using an Ethernet cable.
- From the web browser log into the home page of the WAP.
- Enter the page for wireless security.
- Set your encryption to a protocol and algorithm to one that is supported by your computer (preferably WPA2 and AES) and choose a long secure password.
- Save the changes to your WAP configuration.
- Go back into the properties on the entry on the preferred Network list and adjust them to be the same as the settings on the router.
Router Configuration Hardening
This is just a quick section about a few settings you can change and why it is important to change them. Also about any effects these changes may have.
You will have to click around in the web interface of the WAP to find the settings that I refer to but they are pretty general so they will most likely be there somewhere.
- Disable Unplug and Play (UPnP)
Unplug and Play is a feature that allows programs to open up ports on your router without your intervention. This is a useful feature in some respects but a security risk also. If genuine programs can open up ports then so can programs such as viruses, Trojans and Spyware. If a Trojan managed to get onto your computer and disable your computers firewall you may still be protected as it would not be able to alter the router configuration. It is important to remember that some programs may require this to be left enabled though.
- Disable the Remote Web Admin and wireless web access.
By disabling the Remote Web Admin features you are restricting access to the routers management interface to those who have physical access to the router via an Ethernet cable.
- Change default password.
As mentioned in an earlier section, it is very important that you change the default password to something secure. If you forget the default password you can reset the router to the factory defaults by following the manufacturer’s instructions. Be aware that this will also remove any other settings you have specified such as MAC address filters and encryption.
- Update firmware.
I thought I would include this although I think it’s unlikely anyone will do it. The firmware on the router is the software that is installed on the router that provides all the features such as wireless encryption and MAC address filtering. Sometimes the manufacturer will update the firmware to fix a know vulnerability or to provide an additional feature. It is therefore useful to look at the manufacturers web site occasionally and apply firmware updates as they become available.
- Backup Configuration
After applying all the settings mentioned above find the section in the administration interface that allows you to back up the configuration and perform a backup. It’s best to name the backup with a date and perform a new backup each time you change settings. This way you can roll back to a good configuration if you mess things up.
Further Reading
If you are interested in knowing more about wireless security the links below may be of interest.
