In this post i'll detail how to set up a Windows IAS RADIUS server to authenticate user login on a router.
Windows IAS Server Setup
- Create a Windows Security group with the users you want to allow access to the routers
- Enable the user accounts to have Dial-in Access.
- Install IAS on the server (from Add Remove programs).
- Create a new cisco RADIUS Client, point it to the Router and supply a shared key. Set the Grant Remote Access.
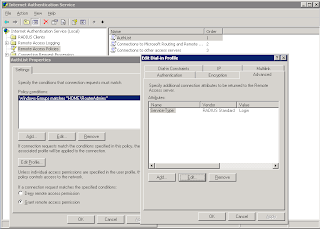
5. Create a new Remote Access Policy with the following settings:
- Windows Group (point this to the group you created)
- Edit the profile and set the autentication to PAP
- Under the advanced tab set the service type value to login & remove Framed-Protocol.
Thats really it. A detailed tutorial on setting up your IAS server can be found here.
Router Setup
Here I am going to configure my router to use AAA Authorization to authorise access by looking at the user credentials in Active Directory (AD). Remember, only AD users in the group I created above will be able to login with their windows credentials.
First I'll talk you through what I'm doing in the following commands.
I'm creating a local user on the router called syn. This is so I can still get into the router if my RADIUS server fails.
I enable AAA and I create a new entry in AAA to point to my RADIUS server (using the default ports) and give it a the key "cisco" to match what we set up on the RADIUS server.
I then enable my ethernet interface on the same LAN as the RADIUS server as the RADIUS source interface and create a AAA authentication login method list called AuthList. This rule will first look to authenticate by RADIUS and then locally if the RADIUS server fails. I then apply the method list to my VTY (Telnet/SSH) ports.
R1>en
Password:
R1#
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#user syn password cisco
R1(config)#aaa new-model
R1(config)#radius-server host 10.0.1.230 auth-port 1645 acct-port 1646 key cisco
R1(config)#ip radius source-interface ethernet 1
R1(config)#aaa authentication login AuthList group radius local
R1(config)#line vty 0 4
R1(config-line)#login authentication AuthList
R1(config-line)#exit
R1(config)#exit
R1#
A detailed tutorial can be found here. Just remember to enable the user account for Dial-in access in the AD account properties.
After setting this up I also needed to configure RADIUS authentication on my Console port and Aux port using the following for each port:
R1(config)#line console 0
R1(config-line)#login authentication AuthList
R1(config-line)#exit
R1(config)#line aux 0
R1(config-line)#login authentication AuthList
R1(config-line)#exit
R1(config)#exit
R1#
Troubleshooting
Debugging on the router can be achieved with the following commands:
R1# terminal monitor
R1# debug aaa authentication
The command below will test a login from the router. You should be able to check your event logs and IAS logs on the RADIUS server to see this account authenticate.
R1# test aaa group radius syn SuperStrongPassword port 1645 new-code