Sunday, February 7, 2010
The websites of two major providers of security products have been hit by hackers.
Leonard said: “The usual suspects have emerged as expected, with Valentine spam emails and Trojans. The public are becoming more aware of these and it is getting harder to trick people this way. Cybercriminals are also taking their efforts to social networks, given its rising popularity and potential to manipulate the user through ‘friend’ messages.
“Organised criminal units have a long history of timing their attacks to coincide with popular occasions in order to achieve maximum success. Valentine’s Day 2009 is a day that is similarly marked on the criminals’ calendar for targeted attacks.â€
Websense has warned of three key signs of fake sites: ‘Broken Hearts’ sites show colourful images such as puppy dogs or a picture of 12 pretty hearts and ask ‘Guess, which one is for you?’. The web page however is one big image and a single click from a tricked user commences the download of Trojans named “onlyyou.exe†or “youandme.exeâ€, which can connect to remote websites to receive commands and send information about the compromised system.
‘I am your friend’ uses social networking tricks to get users to visit fake sites, with Websense claiming that a popular technique at the moment is spam email pretending to originate from social networking sites – complete with love hearts and cartoon characters. Clicking through to the link would download a Trojan designed to steal log in credentials for banking sites.
Seventy per cent of the top 100 most popular websites either hosted malicious content or contained a masked redirect to lure unsuspecting victims from legitimate sites to malicious sites. Specially created malicious sites are in decline as cybercriminals switch to compromising ‘trusted’ websites. Websense claimed that as there is increased confidence in shopping and researching online - a lot of which happens whilst in the office – people are turning to the internet to order flowers, chocolates and other gifts and cybercriminals are compromising these sites and stealing data.
Leonard said: “The underground economy is positively flourishing as companies fail to keep up with security technology. Criminals are taking advantage of the growing number of Web 2.0 properties, which allows user generated content. More than ever we’re seeing websites injected with links to direct users to malicious and compromised sites.
“Since many email security systems lack web intelligence, spammers have also stepped up email campaigns which contain links to malicious web pages. It’s clear that businesses need security with real-time protection, but until this becomes the norm – cybercriminals will continue stealing data and breaking hearts.â€
source : http://www.hacking-news.com/
Wednesday, December 16, 2009
IP Routing - RIP
Using RADIUS to Authenticate Logins
- Create a Windows Security group with the users you want to allow access to the routers
- Enable the user accounts to have Dial-in Access.
- Install IAS on the server (from Add Remove programs).
- Create a new cisco RADIUS Client, point it to the Router and supply a shared key. Set the Grant Remote Access.
- Windows Group (point this to the group you created)
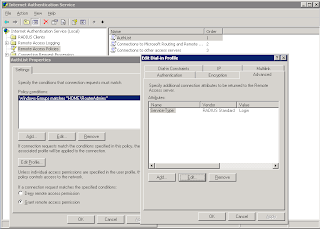
- Edit the profile and set the autentication to PAP
- Under the advanced tab set the service type value to login & remove Framed-Protocol.
After setting this up I also needed to configure RADIUS authentication on my Console port and Aux port using the following for each port:
Backup & Restore IOS and Configs
As with any aspect of computer data, the IOS and the router configs need backing up. This is pretty simple and in this post post I'll show a few different ways of doing this.
copy tftp://10.0.1.3/ios-file-name.bin flash:ios-file-name.bin
- If your IOS is larger than the free space in flash it will overwrite the existing IOS in flash. But be sure not to reboot a router between deleting an IOS file from flash and restoring the new one.
- After restoring a config all interfaces are placed in a shutdown state.
- Restored configs merge into existing configs so if this isn't what you want use the erase command before restoring.
Configuring Router Interfaces
Lab Setup
In this lab I'll have two router and I'll configure them to talk to each other
To start with you might want to clarify exactly which interfaces your router might have. This can be done visually (by looking at the device) or by using some of the excellent show commands.
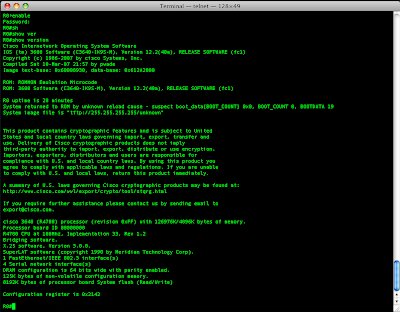
The show version command will print to the screen exactly which interfaces are installed.
R0>en
Ro#show version
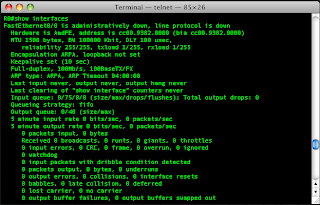
The show interfaces command gives details on the configuration of the interface, setting such as duplex and speed, and it will also show traffic statistics.
R0#show interfaces
If you have many interfaces in your router you can just focus on a single interface using the interface number (remember, slot/port):
R0#show interfaces fastethernet 0/0
From the output I can see that the interface isn't configured. I'll configure that port and then take another look. I'll go into configuration mode select the interface, give it an IP address and subnet mask then tell it not to be in the shutdown state. Remember, by default all ports are in a shutdown state. Another import thing to remember is if you restore your config from a backup the ports will need to be taken out of the shutdown state manually.
R0>enable
R0#configure terminal
R0(config)#interface fastethernet 0/0
R0(config-if)#ip address 192.168.1.1 255.255.255.252
R0(config-if)#no shut
R0(config-if)#exit
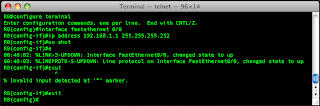
I saw the line come up when I was setting the port up, so now i'll ping my other router.
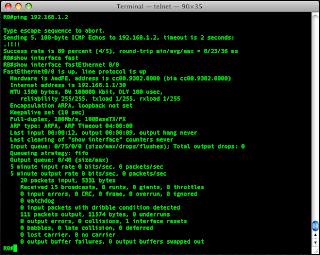
Wel the ping came back fine and after another look at the interface I can see it has the right IP address and the counters are updating nicely.
Another great command for looking at the interface is:
R0#show ip interface fastethernet 0/0
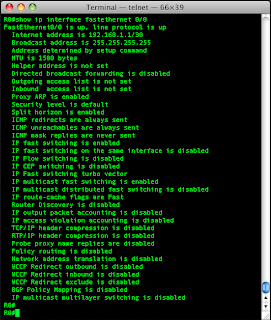
This shows me absolutely everything that is set or can be set on the interface.
And finally one last command for looking at the interface status in a nice condensed format is:
R0#show ip interface brief
Here I see all interfaces, what there IP addresses are and whether they are up or not.
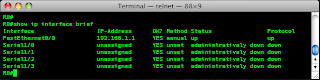
So this has been a quick post on setting up an interface with an IP address and using some handy show commands to check the interface.
Securing Your Router
Right. So I've got my test lab set up. To start with i'll just have one router called R0. I'll demonstrate how to configure the router and secure it.
Securing Your Router
Right. So I've got my test lab set up. To start with i'll just have one router called R0. I'll demonstrate how to configure the router and secure it.